FreqyWM:
Invisible Watermarking based on frequency modulation
Introduction
In a digital age where data ownership and security are paramount, watermarking has emerged as a vital tool for protecting intellectual property, preventing unauthorized distribution, and proving ownership. Traditional watermarking techniques often come with limitations, including noticeable data distortion, low robustness, and high computational complexity. Enter FreqyWM—a cutting-edge solution redefining invisible watermarking through token frequency modulation.
What is FreqyWM?
FreqyWM (Frequency-Based Watermarking) offers a novel approach to embedding ownership marks in datasets without affecting data usability. By subtly modulating token frequencies, FreqyWM ensures the watermark remains imperceptible yet detectable. This approach guarantees minimal distortion, making it ideal for various data types, including text, multimedia, and AI datasets.
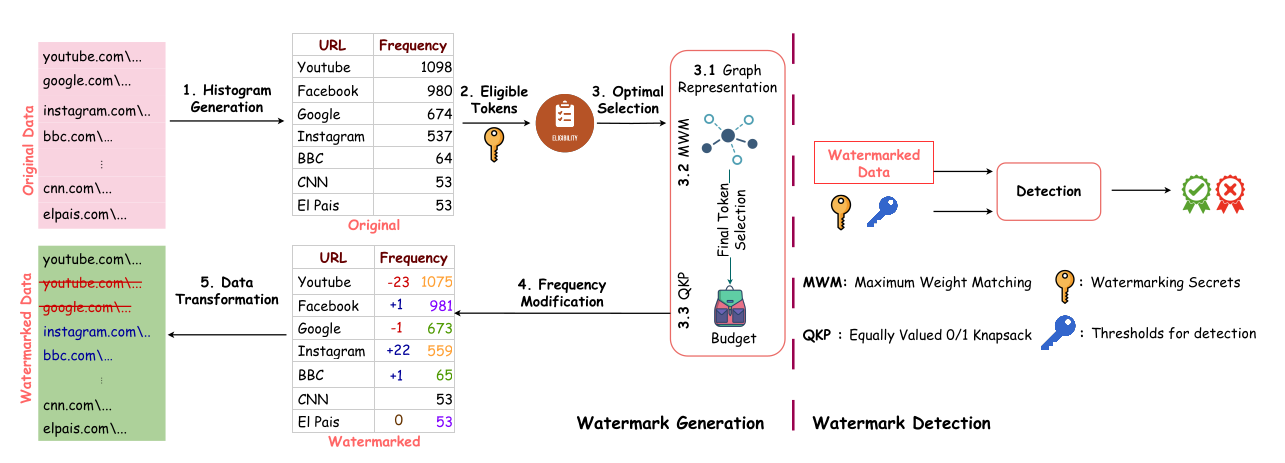
How Does It Work? FreqyWM employs a three-step methodology:
- Token Distribution Identification: Analyzes token distributions in datasets.
- Token Frequency Modification: Slightly adjusts token frequencies to embed the watermark.
- Watermark Extraction and Verification: Detects ownership by comparing modified token frequencies against original values using statistical analysis.
Why FreqyWM Stands Out FreqyWM addresses the challenges of traditional watermarking by:
- Preserving data quality with minimal modifications.
- Providing robust defense against attacks, including guess, sampling, destroy, and re-watermarking attacks.
- Offering scalable and efficient detection techniques.
Comparison with other watermarking techniques:
Security
Built-In Security and Resilience FreqyWM leverages cryptographic principles to ensure high security. It resists adversarial attacks through secret-based modulo computations and hash functions with strong collision resistance. The watermark is distributed across the dataset, making removal nearly impossible without damaging the data. The authors prove that the algorithm is robust againts several types of attcks like:
- Guess attack
- Samplig attack
- Destroy attack
- Re-watermarking attack
References
[1] D. Isler, E. Cabana, A. Garcia-Recuero, G. Koutrika and N. Laoutaris, "FreqyWM: Frequency Watermarking for the New Data Economy," in 2024 IEEE 40th International Conference on Data Engineering (ICDE), Utrecht, Netherlands, 2024, pp. 4993-5007, doi: 10.1109/ICDE60146.2024.00379.
url: https://doi.ieeecomputersociety.org/10.1109/ICDE60146.2024.00379
